Why I Will Never Buy a Lima Device Again
Why You Should Never Use Google Authenticator Again
Reasons why U2F is better than TOTP (onetime password)
In that location can never be plenty security. On the other manus, using faulty or weak protections may merely make you feel safe while you remain exposed to various threats.
Using passwords only is generally a bad idea, something we have known since the starting time of the Internet. We are making progress toward a password-free globe, just in the meantime, many websites offer an additional user account protection with Two-Factor Authentication (2FA).
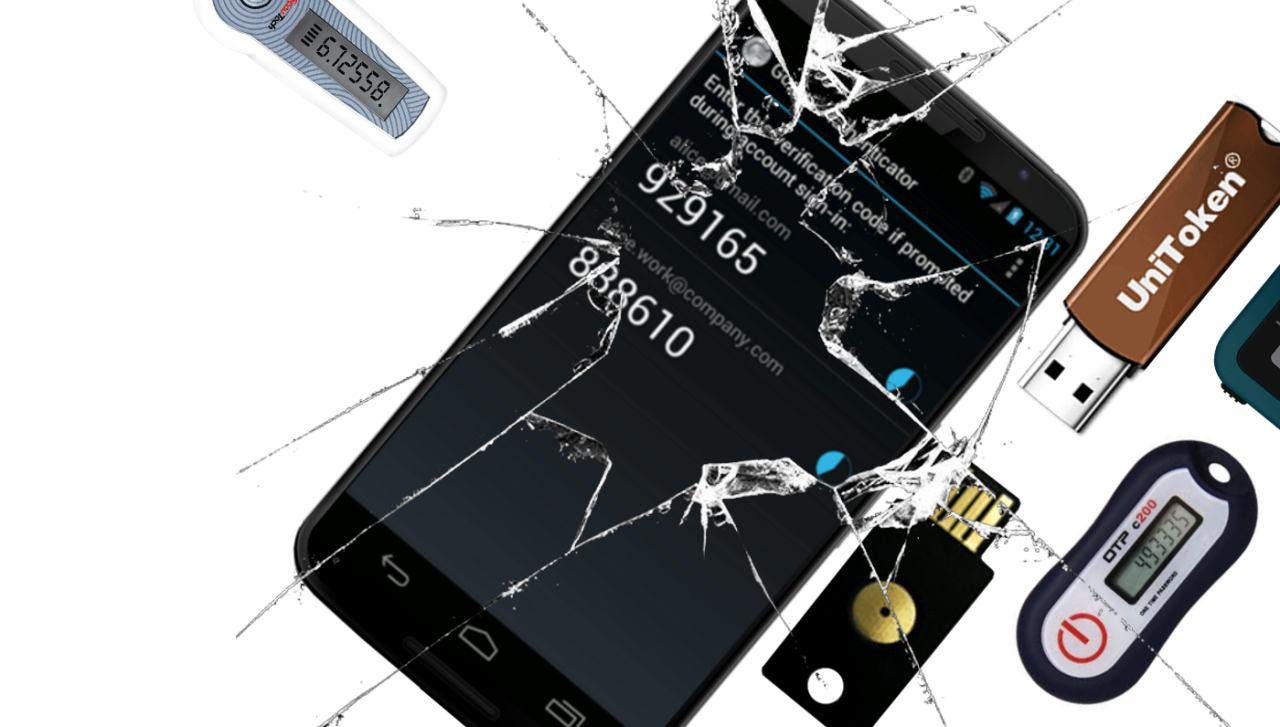
In general, in that location are 2 types of 2FA implementations: Fourth dimension-based Ane-time Countersign (TOTP) and Universal Second Factor (U2F). You may be familiar with the quondam, every bit it is the well-nigh usually used 2FA: at login, you have to enter a one-fourth dimension lawmaking generated by your phone app, a dedicated hardware device, or sent to you via SMS. While unproblematic, there are several shortcomings to this method.
How Does TOTP Work?
Time-based Onetime Countersign (TOTP), popularized mainly by Google Authenticator, verifies your identity based on a shared secret. This clandestine must be shared online between you and the provider.
When logging into a website, your device generates a unique code based on the shared secret and the current time. Then you lot have to submit this code manually. The server generates the exact aforementioned thing, based on the same hole-and-corner, to compare and validate the login request.
Why Is TOTP Inadequate?
While TOTP is very simple to use, it has weaknesses and inconveniences.
- You take to manually input the code at logging in, calculation another step to the procedure.
- Backup is cumbersome. You accept to take boosted steps to support the undercover. Also, the services often offering reserve codes instead of explicitly suggesting to save the secret. If yous lose your secret and log in with a reserve lawmaking, you lot will accept to redo the entire TOTP registration process again.
- Backup codes are sent online, which is often insecure.
- Y'all and Provider share the same clandestine. If an attacker hacks into a company and gains admission to both the password and the secrets database, he/she will exist able to access every account completely unnoticed.
- The clandestine is displayed in plaintext or QR code. It cannot be provided as a hash or with a cryptographic table salt. This also means that the secret is about likely stored in plaintext course, on the servers of the provider.
- The secret can be exposed during the registration, as the provider has to give you a generated secret. Past using TOTP, you take to trust the providers to exist able to protect the secret. But can you?
How Does FIDO/U2F Work?
The U2F standard by the FIDO Alliance was created past technological corporations, such as Google and Microsoft, recognizing the weaknesses of TOTP. U2F uses public-cardinal cryptography to verify your identity (Reddit — Explain Like I'grand Five). In dissimilarity to TOTP, you lot are the only one to know the hugger-mugger ( the private key ).
Benefits of U2F
- No shared underground (private key) is sent over the internet at any time. No confidential data will e'er be shared, thanks to public-key cryptography.
- Easier to employ. No retyping of i-time codes involved.
- Privacy. No personal information is associated with the secret.
- Backup is theoretically easier. Though, non always possible. E.g., you lot cannot support a Yubikey.
Considering with U2F, there is no secret shared and no confidential databases stored by the provider, a hacker cannot merely steal the entire databases to become access. Instead, he has to target individual users, and that is much more costly and fourth dimension-consuming.
Moreover, yous can dorsum up your hush-hush (individual cardinal). On the one hand, it makes you responsible for your security, but it too means that you do not need to trust any company to protect your secrets (private keys).

Trezor — U2F Washed Correct
Trezor is a pocket-size dedicated device designed to store private keys and to serve as an isolated computing environment. Originally invented as a secure Bitcoin hardware wallet, created to protect money, its uses have expanded cheers to the wide applicability of asymmetric cryptography. Trezor tin can now serve as a hardware security token for U2F, but with backup/recovery functions and convenience, which no other production can compare to.
How Does U2F With Trezor Work?
When logging into a website, y'all more often than not authenticate yourself by providing a user name and a password. With Trezor and U2F, yous volition have to additionally confirm the login with a click on your Trezor device.
Unlike some other tokens, Trezor always uses a unique signature for each and every user business relationship registered. Additionally, Trezor brings U2F to a completely new level:
- Easy to dorsum up and recover. Trezor requires yous to back up your and then-called recovery seed during the initial setup of the device. This is a one-fourth dimension process for all functions of the device. The recovery seed represents all the secrets (private keys) generated by the device and can exist used to restore your hardware wallet at any time.
- An unlimited number of U2F identities, that are all saved under i backup.
- The secret is safely stored inside Trezor. It volition never be shared, every bit it tin never leave the device. No viruses or hackers can access them.
- Phishing protection with on-screen verification. Trezor always displays the URL of the website you lot are logging into, and what exactly y'all are about to qualify. You can verify that what was sent into the device is, in fact, what you expected.
- Boosted information on setup, use, and recovery of Trezor for U2F can be found in our blog post here or in the User Manual.
The condom characteristics of disproportionate cryptography fall into the security philosophy of Trezor. With the U2F support in Trezor, we encourage users to utilize all measures bachelor to secure their accounts and identity online.
Interesting Articles:
Here's How an Attacker Can Bypass Your Ii-Factor Hallmark
Calculation a phone number to your Google business relationship can make it LESS secure
Centralized versus Decentralized Networks
About Us
Created past SatoshiLabs in 2014, the Trezor I is the original and most trusted hardware wallet in the world. It offers unmatched security for cryptocurrencies, password management, and serves equally the second cistron in Two-Factor Authentication. These features combine with an interface that is like shooting fish in a barrel to use whether you are a security practiced or a brand new user.
Trezor Model T is the adjacent-generation hardware wallet, designed with the benefits of the original Trezor in heed, combined with a modern and intuitive interface for improved user feel and security. Information technology features a touchscreen, faster processor, and avant-garde coin back up, equally well every bit all the features of the Trezor 1.

Source: https://blog.trezor.io/why-you-should-never-use-google-authenticator-again-e166d09d4324
0 Response to "Why I Will Never Buy a Lima Device Again"
Post a Comment